The world of cybersecurity is in constant flux, demanding that organizations continually reassess their defensive strategies. A traditional focus solely on preventing breaches, while important, is proving insufficient in the face of sophisticated and persistent threats. As highlighted in a recent Illumio podcast episode, "Trust & Resilience: The New Frontlines of Cybersecurity," the very foundation of digital interaction—trust—has ironically become a primary vulnerability exploited by attackers. This necessitates a fundamental shift in perspective.
FRS Pros Blog
If you're like many small and medium-sized business owners, you're juggling countless online passwords… for email, banking, software, supplier portals, and more. It's overwhelming! This often leads to using simple or repeated passwords, which unfortunately opens the door to cyber threats like data breaches, a serious risk for any business. Thankfully, there's a straightforward solution: a password manager.
Small businesses today generate a lot of data. From customer details and sales records to inventory tracking and employee schedules, you need to be able to structure this data so that you can use it effectively. Keeping that data organized and accessible is important, but managing it effectively can often be a hassle. This is where smart database management comes in. When done right, it helps businesses run smoother and often save money.
Does your business have an internal IT department or dedicated IT resource? We know it’s hard sometimes to find the talent you’re looking for, but that doesn’t make it any less important. Here are some of the issues you’ll want to keep in mind if you want to get an IT technician on your staff.
Bring Your Own Device, or BYOD, is a common approach for businesses that want to take advantage of mobile technology to kickstart productivity. Instead of supplying each individual employee with company-owned devices, businesses allow employees to use their own devices for work-related purposes. While this is great on the budget, it’s only really effective (and safe) if the employee prioritizes security on their devices; otherwise, it’s a liability.
The Android operating system periodically receives updates and patches detailed in online publications called Android Security Bulletins. In the March 2025 edition, Google announced that 43 malicious bugs had been resolved, two of which were zero-day vulnerabilities.
Let’s talk about how to implement these fixes and why this is a practice that should reach every aspect of your business’ IT.
It should come as no surprise that cybersecurity is a big challenge for businesses and individuals alike. The problem: life pretty much revolves around being online these days, so there’s no avoiding it. Therefore, it’s your responsibility to ensure that any data you collect from your customers, employees, and other key stakeholders in your business is well-protected, otherwise you will face severe consequences.
In the United States, tax season is prime time for hackers to take advantage of law-abiding, tax-paying citizens. They do this through all kinds of nefarious activities, such as phishing attacks conducted through text messages and emails claiming to be from the Internal Revenue Service. If you want to avoid getting scammed this tax season, be sure to keep the following tips in mind to stay safe while you conduct your typical tax routines.
Hardware is far from the most fun topic for a business owner to learn more about, but that doesn’t diminish its importance. If you want to ensure your business stays ahead of the game, then you need to be strategic about your hardware implementation. Otherwise, you risk falling behind, put your business in danger, and—even worse—imperil your budget. Today, we want to help you get the most out of your hardware, long before you have to invest in anything new.
If you want your business to succeed, you need to take care of your employees, but businesses sometimes let this important task slip in the throes of the day-to-day. Deloitte estimates that around 8 out of every 10 wage workers show signs of burnout. So the question then becomes… What are you doing about it?
If you or your business are worried about cybersecurity, we’d like to say, “Congratulations, you get it!” Too many people fail to take cybersecurity seriously, and with hackers and data breaches making headlines worldwide, you cannot underestimate them. Today, we want to cover how a cybersecurity consultant can save you time, money, and stress over your security systems.
Sometimes problem solving requires you to step away and think about the issue at hand. Consider any great strategist out there and you’ll understand that it takes time and calculation to make moves that will benefit you now and in the future. Today, we’ll explore how you can be more productive through strategic pausing.
How seriously does your business take data privacy? Can you back up your answer with concrete examples of what you do to prioritize that notion? Today, we face a serious threat to both individual and consumer data privacy, so we want to take the time to cover how you can make data privacy a priority in your own life.
Spoiler alert: a business that lacks productivity is unlikely to see any amount of success. One of the best ways to ensure your productivity is to practice patience. How can patience improve your productivity?
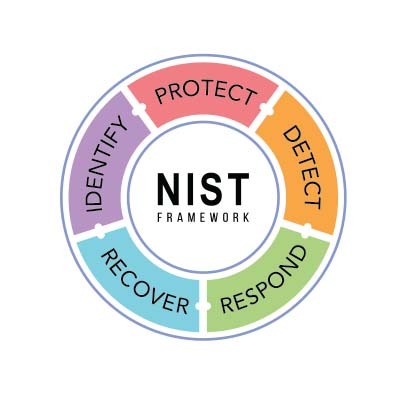
A well-structured framework is essential for establishing effective, consistent policies and strategies. This applies to many areas—including network security. Today, we’re diving into the National Institute of Standards and Technology (NIST) cybersecurity framework, which outlines steps to help safeguard your business.
There’s never been a more dangerous time to run a business. Okay, maybe that’s not necessarily true, but hear me out. With digital technology taking on a greater importance for businesses than ever before, companies have to contend with countless threats—including the ever-popular phishing scams—regardless of their geographical location.
It isn’t rare for people to subscribe to things and only stay subscribed because the cancellation process is so challenging and inconvenient. However, the Federal Trade Commission is looking to stop this, adopting a rule that eliminates the capability for businesses to put hurdles in front of cancellation processes.
Let me ask you something: would you trust a bank that locked its doors for the night but left all its cash in a big pile in the middle of the floor? Probably not—after all, if someone managed to get through the doors, nothing would stop them from helping themselves to the funds inside.
This is effectively how cybersecurity once worked, with the presumption that if someone had access to a network, they had permission to access any data on it. Fortunately, many businesses have made the switch to a better approach, known as zero-trust security.
It’s natural for businesses to rely on their tools, like IT, to achieve success, but if you don’t take care of your systems, it could lead to downtime. You can bypass many of these challenges with the right approach to technology maintenance. We want to highlight some of the proactive methods you can use to keep downtime to a minimum.
Moving is already difficult, but when you factor in your business’ IT, it becomes twice as frustrating and time-consuming. You can make it easier by preparing for the job ahead of time. Today, we want to cover what you can do to prepare for a business IT move well ahead of the scheduled date.