FRS Pros Blog
A compressed file (also known as a zip file) is a handy way to accomplish various tasks, although many people may not know what they are or do. We want to fix that, so we’re going over what a compressed file is and how to make one.
So, what is digital waste?
Digital waste is all the useless data in our data storage that lingers until we do something with it. Extra files no longer needed, old emails and chats, and old, blurry pictures you never have and will never use… all qualify as digital waste. While it’s easy to discount digital waste as an annoyance (which it certainly can be), it creates a much bigger and more serious problem.
The blockchain has made quite a splash, beginning as the technology that powers Bitcoin before branching out into different use cases that many businesses are already taking advantage of. Let’s go over the benefits—and shortcomings—of the various varieties that blockchain now comes in, and how they are commonly used.
As technology advances, gadgets are invented which can be beneficial to not only our social lives but in our business practices. Radio-frequency identification (RFID) is a relatively new technology which businesses have been progressively utilizing.
In the fairy tale of Hansel and Gretel, the titular characters decided to leave a trail of breadcrumbs behind them, so they could find their way back home. While this strategy didn’t work out very well for the siblings, the same concept is used in computing today. We even refer to it as breadcrumb navigation in honor of the German fairy tale.
It doesn’t matter how much of a technology novice someone is, chances are, they’ve heard the term “hacker” before. A favorite character trope of Hollywood films and television dramas, these cybercriminals have appeared in productions like Die Hard and Mr. Robot with varying degrees of accuracy. Below, we explore what makes a hacker, and the kinds that exist in reality.
Thanks to the public cloud, which has amassed around $150 billion in annual revenues, the software as a service model has grown tremendously. In fact, it’s grown by approximately 20 percent a year for the past five years. The public cloud currently houses over a third of all applications used worldwide, making it a significant contributor to the success of software as a service (SaaS). Has your organization begun to take advantage of this phenomenon?
When you sign up for any service online, you will be asked to create a username and a password. Today, we will be going over the purpose of a username and provide you with some best practices on how to create a username that works to your benefit.
The Internet is an amazing tool in and of itself, but like many tools, it can sometimes work better if other tools are used alongside it. These additional tools are called plug-ins. Here, we’ll discuss what a plug-in is, and how they all help us use the Internet a little better.
A computer is a complicated device, so it needs something to help it “think.” Because of this weighty responsibility, the component that serves this purpose is arguably one of the most important of all a computer’s pieces. Known as a CPU, this little chip is truly essential to the computer’s function. For today’s Tech Term, we’ll examine it a little more closely.
Depending on who you ask, RAM will mean a different thing, but in computing, there is only one true meaning. RAM stands for Random Access Memory, and it’s a major component in your computer. But what exactly does it do, and what role does it play in ensuring that your organization stays productive and efficient?
Have you ever wondered where the commonly accepted perception of cyber investigations comes from? You might be surprised to find out that the world of suits, ties, and data terminals is far from the reality of what these investigations are--or, at least, considerably more dramatic. For today’s tech term, we’re going to get to the bottom of this by investigating what computer forensics really looks like.
It seems like everywhere you go, you can see a Chromebook. These specialty laptops have a few features that make them highly desirable in some circumstances, and poorly suited to others. Seeing as ‘Chromebook’ is our Tech Term for this week, why not take a few moments and examine them a little closer?
Most computer users know of the hard drive, but how many actually know what it does? Depending on who you ask, you’ll get different degrees of answers. It’s rare that you’ll encounter the ordinary person who knows what the hard drive is, as well as how it works or what it does. This week’s tech term is the hard drive, so let’s dig in.
The more that people depend on mobile devices and portable computers to get work done, the more businesses have to consider how to manage their organization’s wireless network. The router is the piece of hardware that makes the wireless network possible. Today, we will talk a little bit about the router and how its configuration can dictate the strength, reliability, and security of your business’ wireless network.
There are plenty of topics we reference frequently that may seem a little advanced or complicated at first but are actually pretty simple concepts. Take, for example, virtualization. For today’s tech term, we’ll take a clearer look at this method of computing.
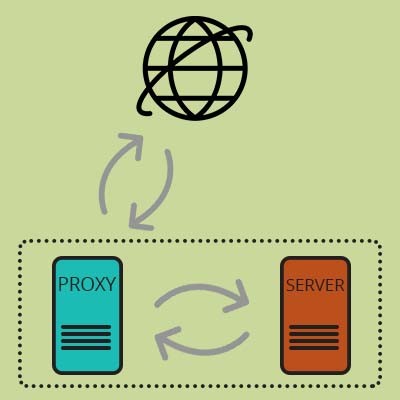
While proxy server is a tech term that is frequently cited, it is not understood by a vast majority of people. Today we will describe what a proxy server is, and why organizations like yours use them.
During your time around computers, chances are high that you’ve heard the phrase “plain text” and the acronym “HTML” tossed around when it comes to your email. If you aren’t sure what these statements refer to, we’re here to help. Today, we’ll examine both HTML and plain text to produce a better understanding of these tech terms.