FRS Pros Blog
When the People You Trust Phish You
Having success in business often relies on developing trustworthy relationships. You have to trust your vendors and suppliers to get you the resources you need, you need to trust your staff to complete their tasks without putting your business in harm's way, and you need to trust your customers to buy the products and services that you offer. Running counter to these necessary bonds of trust are people actively soliciting people’s time, energy, money, and attention for their own selfish purposes.
Cybercriminals don’t care what kind of good will you’ve forged, all they want is your data or access to your network. This blind determination is a major threat to businesses like yours. One of the most prevalent scams is what is called a Display Name Spoof. It isn’t just your regular phishing scam, and today, we’re going to teach you everything you need to know to ensure that you aren’t a cybercriminal’s next victim.
What is Display Name Spoofing?
Display name spoofing is a spear phishing tactic where hackers will target an individual—who typically has access to the network or resources that the hacker wants access to—and sends them a vaguely worded email that is seemingly sent from a trusted source, often an authority figure. Since the email address and title look legitimate, subordinates who forsake security for alacrity can put your whole business in jeopardy.
It works like this: Many professional emails will have a signature. Display name spoofers use this to their advantage. What they will do is target a person, research them to find someone that could potentially get them to act impulsively, and use that information to phish the user. Below is an example of a display name spoof phishing attempt:
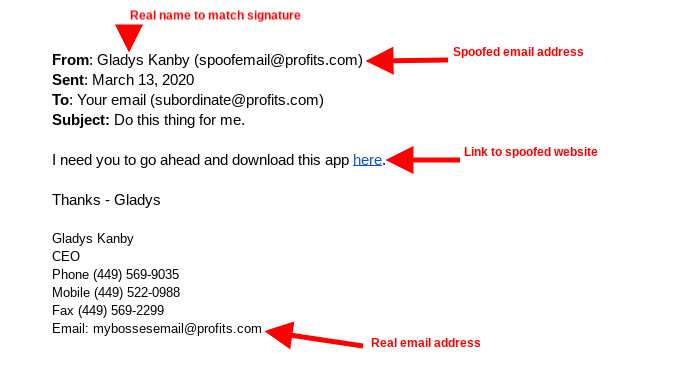
As you can see, the only thing that looks illegitimate here is the actual email address and since some email clients don’t actually show the address by default, you wouldn’t blame a dutiful employee for following the instructions in the spoofed email.
What Can You Do to Combat Display Name Spoofing?
At your business, you have cameras, You have locks on the doors. You’ve developed secure access control procedures to ensure your employees have the authorizations they need to do their jobs. Why would your strategy change when aiming to protect your business’ most important asset?
Just like with physical security, you need a strategy to protect your digital assets. Part of that strategy has to confront the fact that your business is going to get phished and that it is your responsibility to ensure that your employees are well trained, and therefore knowledgeable about how to identify and respond to these situations.
Here are a few tips on how to ascertain if a message is legitimate:
- Thoroughly inspect both the name and sender’s email address before you take action.
- Check the content for misspellings or completely incorrect uses of grammar.
- Consider if the sender would send a message asking you to take cavalier action.
- Consider if the sender would ask you to send them authorization credentials through email.
If there is any reason that the recipient has a notion that the email is not legitimate, implore them to verify. Getting a verification of the email’s legitimacy typically takes minutes and can really help eliminate the risks that display name spoofing can bring to your business.
If you need help understanding how to identify phishing tactics, train your employees to do the same, and knowing what steps to take when you realize you are dealing with a phishing attack, contact the IT professionals at FRS Pros today at 561-795-2000.



